A Crypto Wallet Stealer delivered via Telegram has been found in the open according to Juniper Threat Labs. The trojan uses Telegram to take over crypto wallets. It replaces the users’ wallet with its own.
Juniper Threat Labs discovered a new Trojan-delivered spyware that uses Telegram to exfiltrate stolen information. Using Telegram as a Command and Control (CnC) channel allows the malware some anonymity, as Telegram is a legitimate messaging application with 200 million monthly active users.
The malware is being advertised on black market forums as “Masad Clipper and Stealer”. It steals browser data, which might contain usernames, passwords and credit card information. Masad Stealer also automatically replaces cryptocurrency wallets from the clipboard with its own.
Masad Stealer sends all of the information it collects – and receives commands from – a Telegram bot controlled by the threat actor deploying that instance of Masad. Because Masad is being sold as off-the-shelf malware, it will be deployed by multiple threat actors who may or may not be the original malware writers.
What it does
This malware is written using Autoit scripts and then compiled into a Windows executable. Most samples we have seen are about 1.5 MiB in size, however, Masad Stealer can be found in larger executables as it is sometimes bundled into other software.
When Masad Stealer is executed, it drops itself in %APPDATA%\folder_name}{file_name}, where folder_name and file_name are defined in the binary. Examples include amd64_usbhub3.inf.resources and ws2_32.exe, respectively. As a persistence mechanism, mMasad Stealer creates a scheduled task that will start itself every one minute.
After installing itself, Masad Stealer starts by collecting sensitive information from the system, such as:
- Cryptocurrency Wallets
- PC and system information
- Credit Card Browser Data
- Browser passwords
- Installed software and processes
- Desktop Files
- Screenshot of Desktop
- Browser cookies
- Steam files
- AutoFill browser fields
- Discord and Telegram data
- FileZilla files
It zips this information into a file using 7zip utility, which is bundled into the malware binary.
Using a hardcoded bot token, which is basically a way to communicate with the Command and Control bot, Masad Stealer sends this zip file using the sendDocument API.
In order to communicate with the Command and Control bot, Masad Stealer first sends a getMe message using the bot token to be able to confirm that the bot is still active. Upon receiving this request, the bot replies with the user object that contains the username of the bot. This username object is useful for identifying possible threat actors related to this malware. This is an important consideration because of the off-the-shelf nature of this malware – multiple parties will be operating Masad Stealer instances for different purposes.
Clipping Routine
This malware includes a function that replaces wallets on the clipboard, as soon as it matches a particular configuration. Below are the regular expressions and supported wallets that it matches against the clipboard data:
Below is a list of coins/wallet it tries to clip:
- Monero
- Bitcoin Cash
- Litecoin
- Neo
- Web Money
- ADA
- ZCASH
- DogeCoin
- Stratis
- QIWI Pay
- Bicond
- Waves
- Reddcoin
- Qtum
- Payeer
- Bytecoin
- Bitcoin
- Black Coin
- VIA
- Steam Trade Link
- Bitcoin Gold
- Emercoin
- Lisk
- Ethereum
- Dash
- Ripple
- Yandex Money
If the clipboard data matches one of the patterns coded into Masad Stealer, the malware replaces the clipboard data with one of the threat actors’ wallets, which are also found in its binary. Below are the bitcoin and monero wallets found in one of the samples:
Bitcoin: 1AtwyYF2TGR969cyRDrR2XFDqSPzwCXKfe
Monero: 42Mm9gjuUSmPNr7aF1ZbQC6dcTeSi1MgB1Tv41frv1ZRFWLn4wNoLH3LDAGn9Fg2dhJW2VRHTz8Fo9ZAit951D2pDY8ggCR
Below is a snapshot of the bitcoin wallet transaction, as of this writing. This wallet has already received around $9,000 USD equivalent of bitcoins (as of Sept 15, 2019), which may or may not come from the activity of this malware.
Attack Vector
Based on their telemetry, Masad Stealer’s main distribution vectors are masquerading as a legitimate tool or bundling themselves into third party tools. Threat actors achieve end user downloads by advertising in forums, on third party download sites or on file sharing sites. Below are the currently known list of software that Masad Stealer has been seen mimicking:
ProxySwitcher (legitimate version here: https://www.proxyswitcher.com/)
CCleaner.exe (legitimate version here: https://ccleaner.com/)
Utilman.exe (legitimate version comes with Windows)
Netsh.exe (legitimate version comes with Windows)
Iobit v 1.7.exe (legitimate version here: https://www.iobit.com/)
Base Creator v1.3.1 [FULL CRACK].exe (there is no legitimate version)
EXEA HACK CRACKED (PUBG,CS GO,FORTNITE,GTA 5,DOTA).exe ( there is no legitimate version)
Icacls.exe (legitimate version comes with Windows)
WSManHTTPConfig.exe (legitimate version comes with Windows)
RADMIR CHEAT MONEYY.exe (there is no legitimate version)
Tradebot_binance.exe (legitimate version here: https://tradesanta.com/en)
Whoami.exe (legitimate version comes with Windows)
Proxo Bootstrapper.exe (this is actually a reasonably popular form of malware)
Fortniteaimbot 2019.exe (there is no legitimate version)
Galaxy Software Update.exe (https://www.samsung.com/us/support/answer/ANS00077582/)Downloads additional malware
Some samples of Masad Stealer have the capability to download additional malware. Some samples that download other malware, usually a miner, from these URLs:
https://masadsasad[.]moy.su/base.txt (miner)
https://zuuse[.]000webhostapp.com/mi.exe (miner)
http://37[.]230.210.84/still/Build.exe
http://37[.]230.210.84/still/SoranoMiner.exe
http://187[.]ip-54-36-162.eu/steal.exe
http://bgtyu73[.]ru/22/Build.exeThreat Actors
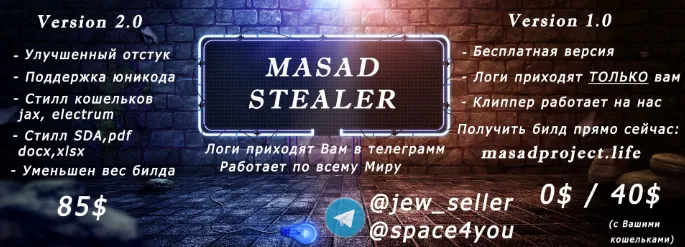
This malware is being advertised in several hack forums as Masad Stealer. It starts with a free version and ladders up to versions asking up to $85, with each tier of the malware offering different features.
There is at least one dedicated website (masadproject[.]life) in existence to promote the sale of Masad Stealer. The developers have also created a Telegram group for their potential clients, and presumably to offer tech support. At time of writing, this group has more than 300 members.


